A recent campaign, unearthed by researchers at INKY, is the latest example of exploitation of a legitimate cloud service. The campaign impersonates the U.S. Small Business Administration (SBA), targeting small businesses that are unaware of the fact that the SBA recently stopped accepting applications for COVID-19 relief loans or grants.
The element that makes this campaign stand out from the others is the exploitation of a well-known and familiar cloud service to host the phishing page: Google Forms.
Threat actors continue to abuse Google Forms to deliver phishing pages, and the reasons are simply summarized as:
- It is a service trusted by both consumers and businesses.
- Bad actors can easily set up their malicious pages or compromise a legitimate account, to host phishing content and harvest data, or even distribute malware.
- It is easier to evade detection since the domains have high reputation and won’t normally appear in threat intelligence feeds.
- The traffic is encrypted so it is not easily inspected by legacy on-prem technologies.
- Additionally, legacy technologies cannot differentiate instances, making the enforcement of separate security policies for managed cloud services and non-corporate or personal instances of managed cloud services impossible.
While Google allows the reporting abuse of its services and has some mechanisms in place to detect phishing pages (for example recognizing specific keywords in the forms), threat actors continue to be quite creative, even with all the limitations imposed by the layout. The page is quite simple, a disclaimer recommends to never submit passwords, and it’s clearly stated that Google neither created nor endorsed the content, but nonetheless, the trust of the victims is high because of the use of a legitimate page, and this increases the chances of success of the attack.
Phishing campaigns tend to exploit global events, and despite the level of attention on the pandemic constantly decreasing, COVID-19 continues to be an effective phishing lure. The exploitation of a trusted cloud service makes this campaign even more effective.
How Netskope mitigates the risk of cloud phishing
Google Forms (and Microsoft Forms) are some of the applications where Netskope can enforce granular access control and instance recognition. This allows security teams to govern activities on non-corporate instances, preventing the submission of credentials into a rogue form (or even the download of malware).
To act more granularly, a simple DLP rule, placed after any legitimate service, can prevent the submission of corporate credentials into rogue forms, whether they are built on a cloud app or a regular domain. In the following example (a real phishing page hosted on Google Forms), the policy prevents the submission of a corporate credential.
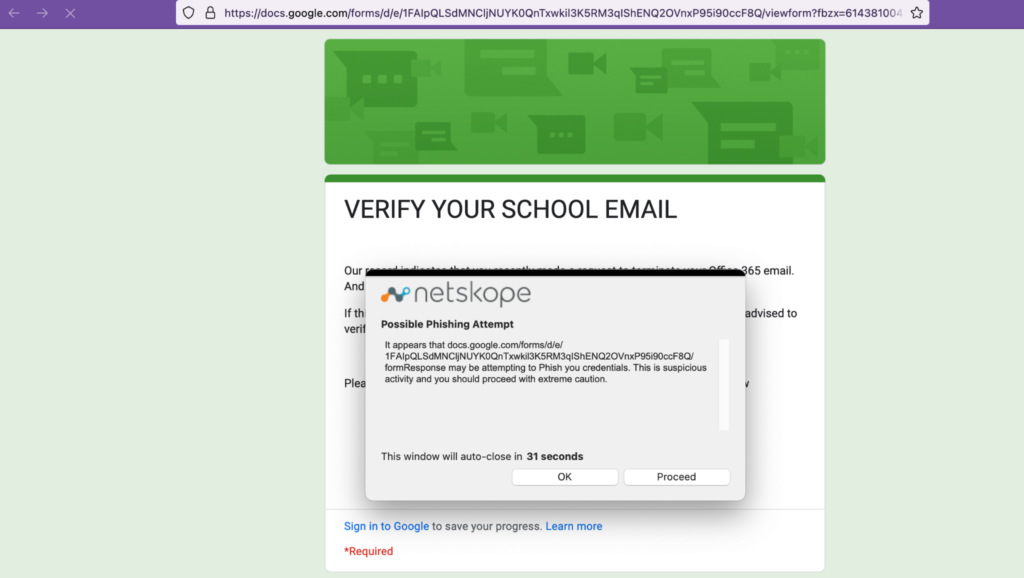
Last but not least, proprietary threat intelligence from Netskope Threat Labs, part of the Netskope threat protection, is able to detect phishing pages, preventively blocking the access, even if they are hosted on a legitimate cloud application. The same applies if the legitimate service is abused to deliver malware, as Netskope can scan the artifact with its multi-layer engine including an AV engine, advanced heuristics, machine learning classifiers, and sandboxing.
Stay safe!




 Retour
Retour 





















 Lire le blog
Lire le blog